What is “Living Off the Land/Orchard”?
“Living off the land” is a cybersecurity term describing attacks that use legitimate, pre-existing system tools instead of custom tools. Rather than bringing their own malicious software, attackers leverage the binaries, scripts, and libraries already installed on target systems. “Living Off the Orchard” is the macOS-specific variant of this concept - a play on Apple’s association with orchards.
Why Attackers Choose This Approach
- 🎯 Easily Accessible - No software installation required
- 👻 Reduced Footprint - No external tools needed, creating minimal filesystem artifacts
- 🫥 Blends with Normal Activity - Blend seamlessly with legitimate operations
- 🛡️ Evades Detection - Bypasses signature based detections by exploiting trust in system signed binaries
What Can AppleScript/JXA Do?
AppleScript and JXA are powerful automation tools pre-installed on every Mac. While designed for legitimate system administration, these capabilities can be weaponized for:
- Persistence mechanisms (login items, launch agents)
- Credential access (password prompts)
- Discovery operations (system information, user enumeration)
- Defense evasion (hidden windows, execution delays, log deletion)
- Collection (clipboard access, screenshot capture)
Why a Dedicated AppleScript Testing Framework?
While LOOBins and Atomic Red Team provides extensive macOS coverage, AppleScript and JXA deserve specialized focus.
Making LOAS a separate framework allows for:
-
Specialized Focus: Deep dive into macOS specific scripting nuances, TCC permissions, and application automation that would be lost in a general-purpose framework.
-
Multiple Execution Vectors: Each LOAS test can be executed through five different methods (CLI, script files, Swift, applets, binaries), each generating distinct detection telemetry. Adding this complexity to Atomic Red Team would be unwieldy.
-
Parameterized Testing: LOAS bridges the gap between documentation and testing. Unlike documentation libraries (LOLBAS, LOOBins, GTFOBins) that catalog techniques with example usage, LOAS delivers executable, parameterized tests designed for automated security validation.
-
Seamless Integration: LOAS uses a YAML specification similar to Atomic Red Team’s format. Conversion scripts transform LOAS tests into Atomic Red Team atomics, making integration seamless if you already use Atomic Red Team.
Real-World Threat Landscape
Threat actors have consistently demonstrated the effectiveness of AppleScript and JXA in real-world attacks:
-
OSX.Dok (2017): Banking trojan that leveraged AppleScript to create login items for persistence, prompting users for credentials to gain privilege escalation.
-
NetWire (2019): Remote access trojan observed using AppleScript for establishing persistence through login items on compromised macOS systems.
-
XCSSET (2020): Sophisticated macOS malware that used JXA extensively to check XProtect versions, evade detection, and steal Safari cookies and credentials.
-
Atomic Stealer (2023): Modern info-stealer that uses AppleScript’s Finder automation to copy Safari’s BinaryCookies files, bypassing traditional file access detection.
See It In Action
Here’s an example of how AppleScript can be used to prompt for credentials:
set userPassword to text returned of (display dialog "macOS Security Update" & return & "Enter your password to continue:" default answer "" with icon 1 with hidden answer)-- Credential now captured in userPassword variable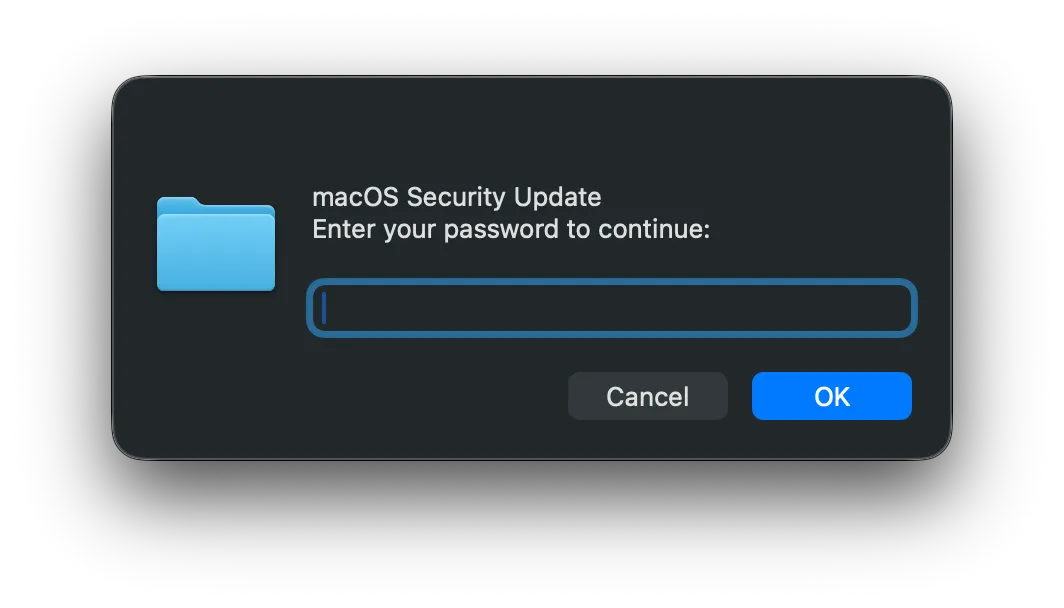
To your users, this looks like a legitimate system prompt. To your SIEM, it might look like nothing at all.