Hello everyone! 👋
I’m excited to release the Atomic Red Team MCP Server - a tool that has transformed my adversary emulation workflow significantly. But before diving into the technical details, let me tell you why I built this.
⚠️ The Problem That Sparked This Tool
As someone who regularly works with threat intelligence and detection engineering, I found myself repeating the same tedious process over and over.
You probably know this pain too:
You get threat intel about a new ransomware campaign. First, you spend 20 minutes sifting through atomic-red-team and others, searching for tests that match the TTPs. Half the time, the perfect test doesn’t exist. So you craft a custom test, validate the YAML syntax, execute it in your lab, debug why it failed, fix the test, run it again, and finally confirm it triggers your detection rules.
What should be a 5-minute task turns into hours of manual work. There had to be a better way. This is where AI-powered automation changes everything.
🤖 Enter AI-Powered Adversary Emulation
What if I could just ask my AI assistant to handle all of this? Instead of manually searching and creating tests, what if I could simply say:
- Find atomic tests for Conti ransomware techniques based on this threat intel report
threat-intel-report-here→ Get instant, relevant results - Create a test to extract login credentials from Chrome browser → Get a validated, ready-to-execute atomic test
- Execute the atomic which creates a login item in macOS and show me the results → Get full execution output and analysis
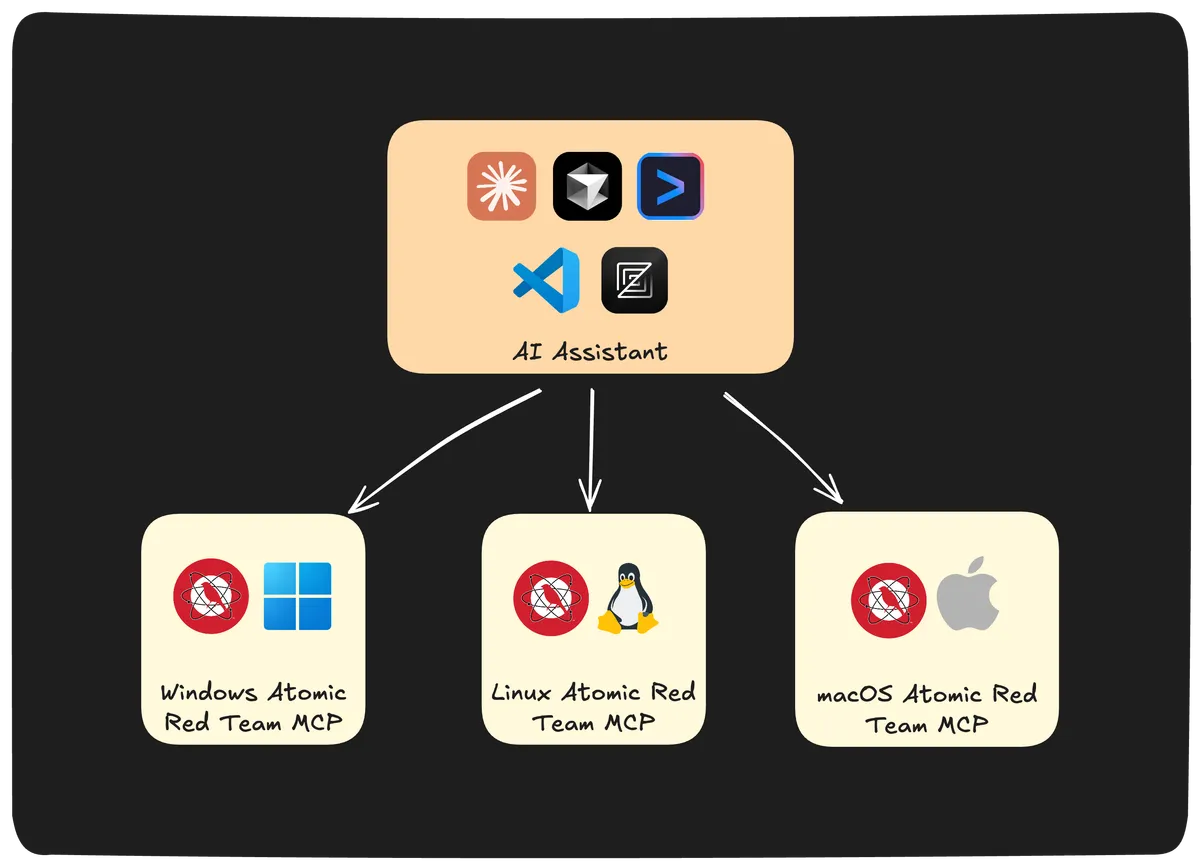
The Atomic Red Team MCP Server makes exactly this possible. It brings 1500+ atomic tests directly into Claude, VSCode, Cursor, and other AI assistants, transforming security testing from manual grunt work into natural conversations, reducing multi-hour processes to minutes.