💭 What Is MCP?
Model Context Protocol (MCP) allows AI assistants like Claude to directly interact with external tools and databases instead of relying on copy-paste workflows between systems. Before MCP, you’d search GitHub for atomic tests, copy YAML to Claude, get responses, then manually transfer everything back to your terminal - essentially acting as a human API bridge.
With MCP, Claude can directly query atomic test databases, validate YAML syntax, and execute commands within the same conversation context. It’s like giving your AI assistant API access to your security toolchain rather than making it work through you as a proxy. This eliminates the context-switching overhead that kills productivity in security workflows.
✨ Key Features
- 🔍 Search 1500+ atomic tests by technique ID, name, or platform
- ⚡ Create new tests with AI assistance following best practices
- ✅ Validate created atomic test against YAML schemas
- 🎯 Execute tests in controlled environments (optional, disabled by default)
⚡ Real World Scenarios
Ready for some practical magic? Here’s what becomes possible:
Scenario 1: Threat Intel Analysis
You receive a threat report about the new macOS Stealer. You need to test your defenses.
Try this:
Example
Analyze the threat intelligence report at threat-intel-report-link-here. First, identify all TTPs mentioned in the report and cross-reference them against the existing Atomic Red Team library to find matching atomic tests. For any TTPs that don’t have corresponding atomics, generate new atomic tests. Finally, compile everything into a structured playbook YAML file with entries formatted as:
- auto_generated_guid: abcdef-abcd-abcd-abcd-abcdef name: Atomic Test name 1 technique_id: T1000
- auto_generated_guid: abcdef-abcd-abcd-abcd-abcdef name: Atomic Test name 2 technique_id: T1000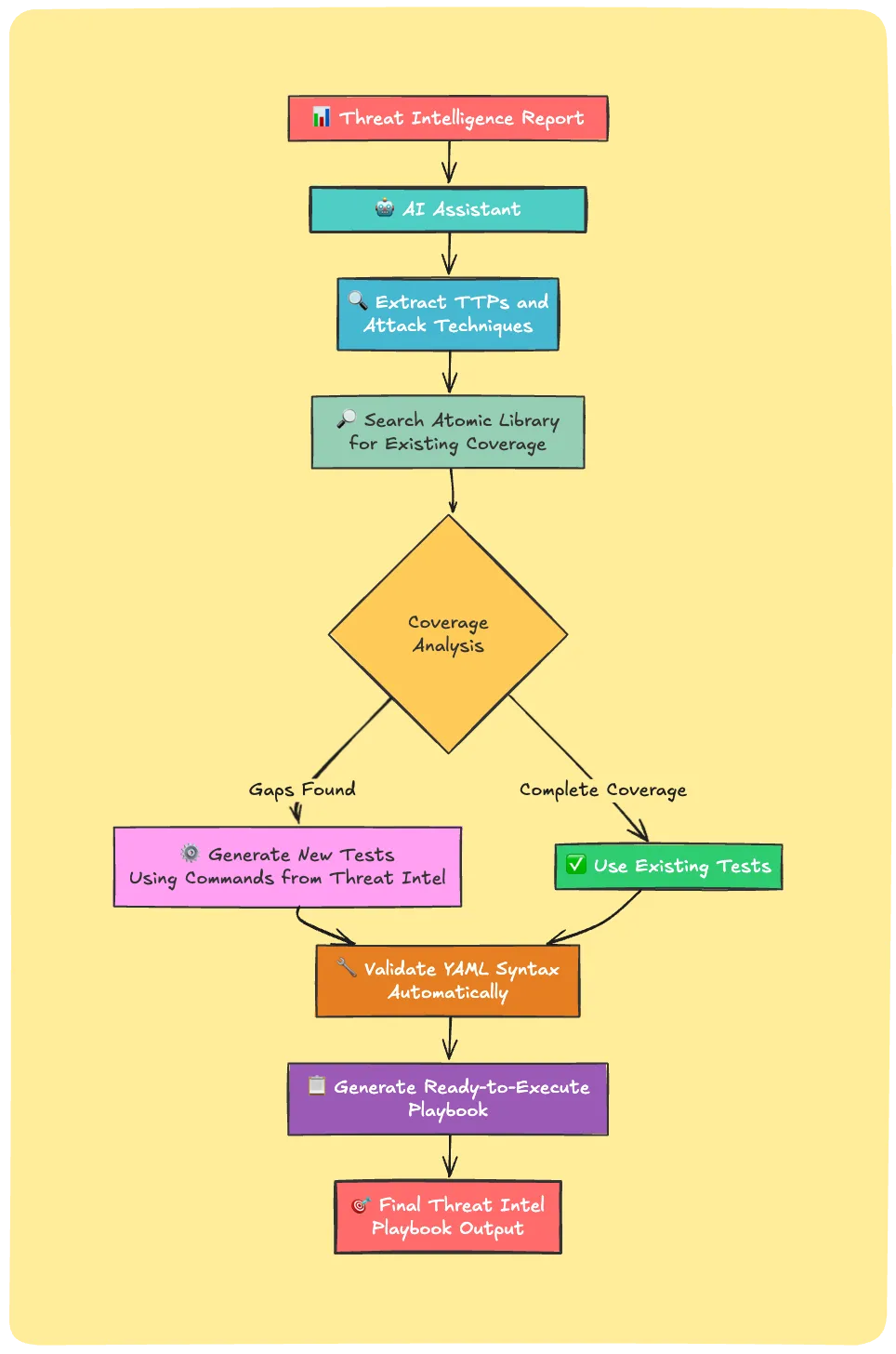
Behind the scenes, the AI assistant will
- Extract TTPs and attack techniques from the report
- Search the atomic library for existing coverage
- Generate new tests for missing techniques using actual malware commands
- Validate all YAML syntax automatically
- Compile everything into a ready-to-execute playbook
Traditional approach: 45+ minutes, with MCP: 5-10 minutes
Scenario 2: Detection Rule Validation
Your team deployed a new detection rule targeting Cloudflare tunnel abuse - a technique increasingly used by threat actors for persistence and C2 communication.
Example
I need to test my ‘Cloudflared Tunnel Execution’ detection rule that flags cloudflared tool usage for maintaining persistence. Find existing atomic tests that would trigger this, or create a new test using techniques from https://lottunnels.github.io/lottunnels/Binaries/cloudflared/
What your AI assistant delivers:
- Searches atomic red team library for cloudflared-related tests
- Analyzes the provided documentation for attack patterns
- Creates a new atomic test if it doesn’t already exist
- Outputs validated, contribution-ready YAML
- (Optional) Chain with SIEM/SOAR MCP integrations for automated validation. Check out Claude found the APT by Michael Haag for a real-world Splunk MCP example.
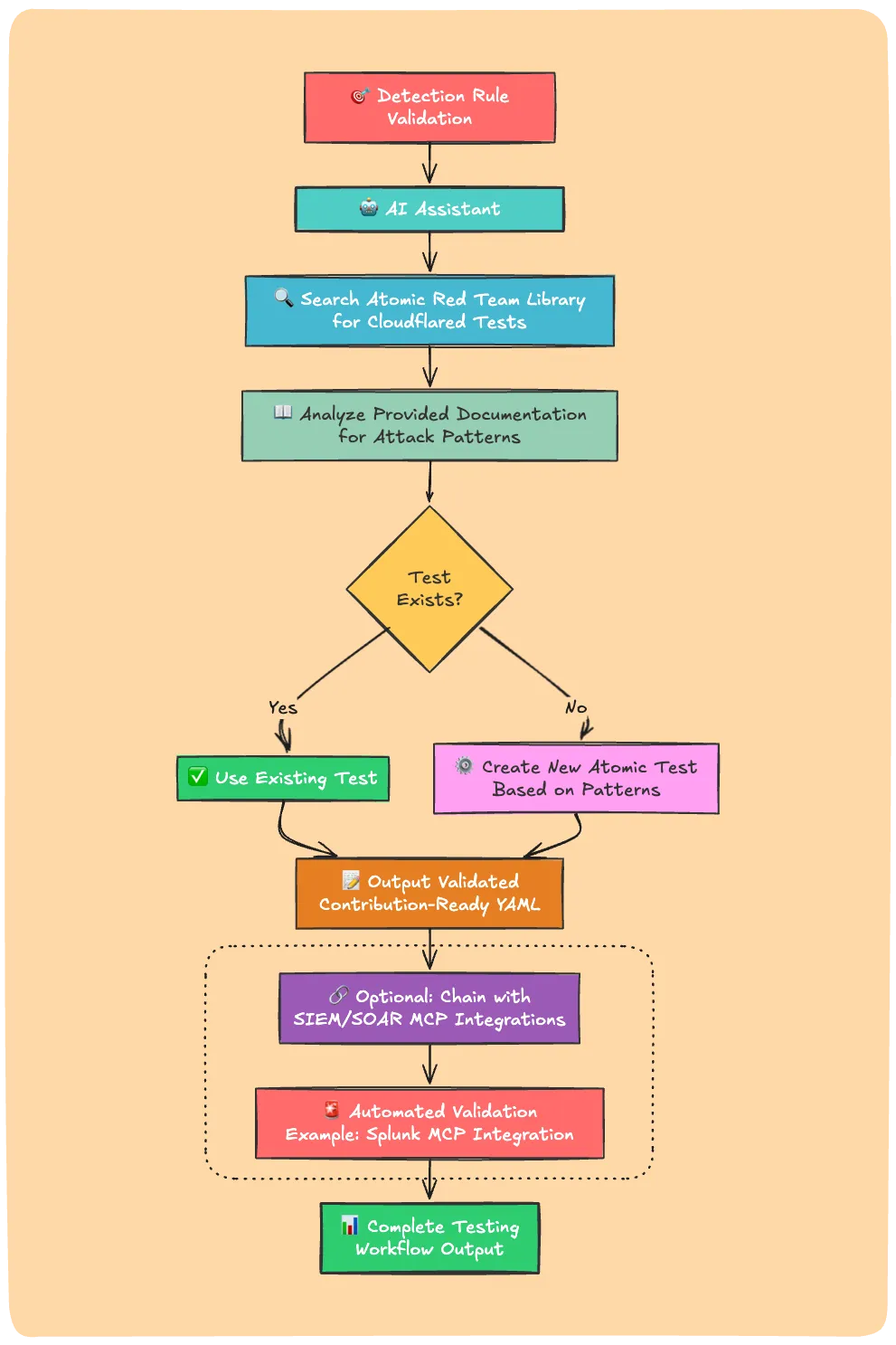
Traditional approach: 30+ minutes, with MCP: 3-5 minutes
🛠️ Troubleshooting
AI not recognizing your requests? Add “using atomic-red-team MCP” to your prompt. If issues persist, start a fresh chat conversation.
🚧 Limitations
- Complex multi-stage campaigns may need manual breakdown.
- Environment-specific payloads require custom modification.
- Generated tests may need tuning for your specific infrastructure.
- If generated tests seem off-target, include specific threat intel reports or attack documentation in your prompt for better accuracy.
🎉 Ready to streamline your security testing?
- Source code: GitHub
- Install in 5 minutes: Installation Guide
- Try your first query: “Show me all osascript tests”
- Found a bug? Create an issue
- Questions? Find me on Atomic Red Team Slack
- Ready to see the magic happen? Checkout Atomics on a Friday for a live demo of the tool on YouTube
Give it a try!
Coming next: Run Atomic Red Team MCPs across Windows, Linux, and macOS with centralized AI assistant control
Note: Huge thanks to Michael Haag for the inspiration with his “Claude found the APT” work - I’m totally borrowing his clever naming convention for “Claude becomes the APT.”