Purple team exercises face a fundamental challenge: while attacks have become more sophisticated and cross-platform, our testing approaches remain fragmented. Security teams juggle platform-specific tooling, manual result correlation, and the constant context switching between testing environments.
The solution? AI-powered orchestration that transforms rigid automation into intelligent, conversational security testing. In this post, you’ll discover how to transform your AI assistant into a multi-platform threat orchestrator that can simultaneously execute atomic tests across Windows, Linux, and macOS. We’ll walk through:
- Setting up MCP servers on all three major operating systems
- Centralized configuration that connects multiple servers to one AI assistant
- Realistic attack scenarios like multi-platform persistence and protocol tunneling
- Advanced orchestration where Claude manages entire multi-OS attack campaigns
By the end, you’ll have Claude coordinating distributed atomic tests across your entire infrastructure through simple natural language commands like “Execute System Network Configuration Discovery atomics on all platforms and give me a consolidated report.”
This post continues from Part 1, where we saw how Claude transforms from a helpful AI assistant into a sophisticated adversary emulation engine. Now, we’re taking it to the next level: multi-platform orchestration.
Most foundational concepts—such as what MCP is, how Atomic Red Team MCP works, and the core introductory use cases—are thoroughly explained in Part 1 of this series. If you haven’t read Part 1 yet, I recommend starting there to get essential background before exploring the advanced orchestration techniques and multi-platform workflows described in this post.
The Multi-Platform Challenge
Adversary emulation has evolved beyond manual coordination—tools like OpenAEV, Caldera, and other adversary emulation platforms already solve the basic multi-platform execution problem. You can absolutely orchestrate execution of atomic tests across Windows, Linux, and macOS using these established frameworks.
But here’s what’s still missing: intelligent, conversational orchestration.
Current tools require you to:
- Learn platform-specific interfaces and configuration syntax
- Pre-plan attack sequences in their native formats
- Context-switch between the orchestration tool and your analysis workflow
- Manually interpret results and plan follow-up actions
Want to test registry persistence on Windows, then immediately adapt based on results? You’re still configuring playbooks, navigating web interfaces, or scripting custom logic.
The real breakthrough isn’t just orchestration— it’s AI-powered orchestration that can analyze, learn, and adapt to your testing needs. What if you could simply say: "Execute registry persistence on Windows, analyze the logs using Splunk MCP, then recommend and run the best Linux persistence technique that would fit this attack scenario XYZ"?
That’s where MCP orchestration transforms the game. You get the infrastructure orchestration of existing tools combined with the intelligent reasoning of LLMs, all through natural language instead of configuration files.
Enter the Cross-Platform C2… Er, AI Assistant
What if you could coordinate atomic tests across all platforms simultaneously using natural language? What if Claude could become your universal threat orchestrator, speaking fluent Windows, Linux, and macOS?
That’s exactly what multiple MCP servers enable. By running Atomic Red Team MCP servers on different platforms and connecting them to a single AI assistant, you create a unified testing interface that enables centralized command and distributed execution.
Here’s the architecture that makes it possible:
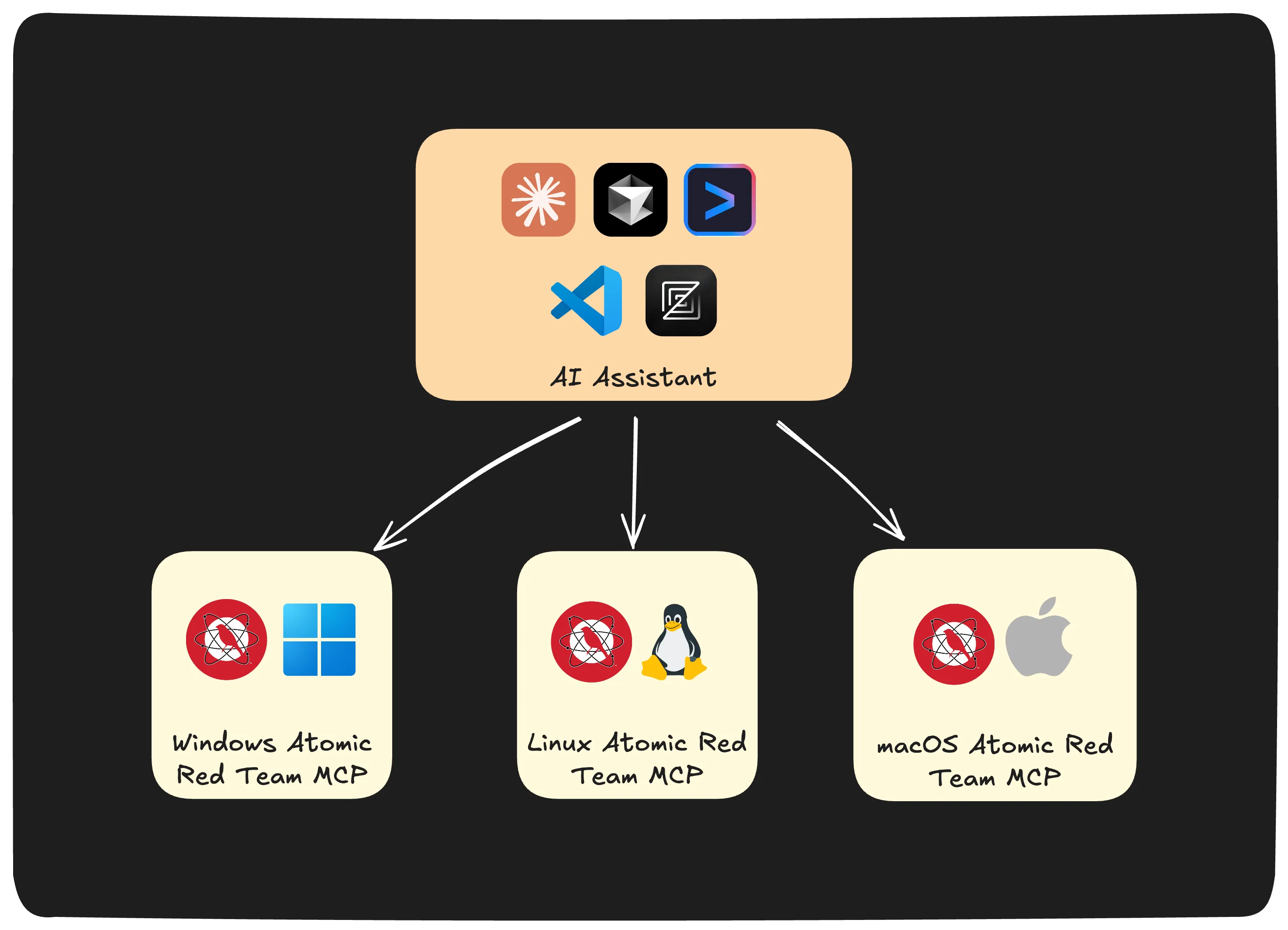
Setting Up Your Distributed Testing Infrastructure
Prerequisites
Before You Begin
Ensure you have the following installed on each target platform:
All Platforms:
- uv (Python package manager) — we’ll show installation commands below
- Network connectivity between client and servers
- Administrative/sudo privileges for service installation (production deployments)
Client Machine:
- npx (comes with Node.js) for MCP remote connections
- Your AI assistant client (Claude Desktop, Cursor, etc.)
Network Requirements:
- Port 8000 (or custom port) accessible between client and servers
- Firewall rules configured to allow inbound connections
Optional but Recommended:
- SSH access to each server (for secure tunneling)
- Isolated test environment (VMs, containers, or dedicated test network)
- SIEM/SOAR MCPs (Splunk, etc.) and ticketing system MCPs (Jira, etc.) for automated detection correlation and workflow integration
Step 1: MCP Server Deployment
Deploy MCP servers across your target platforms (Windows, Linux, and macOS). Make sure to save the authentication tokens from each deployment as these are needed to connect your AI assistant to the servers.
💡 Tip: Always test in a lab before deploying on production systems
Windows deployment (PowerShell):
# Install uv
powershell -ExecutionPolicy ByPass -c “irm https://astral.sh/uv/install.ps1 | iex”
# Generate secure authentication token
$TOKEN = -join ((48..57) + (65..90) + (97..122) | Get-Random -Count 32 | ForEach-Object {[char]$\_})Write-Host "Windows server token: $TOKEN" -ForegroundColor Green
# Configure and launch
$env:ART_MCP_TRANSPORT = "streamable-http"$env:ART_EXECUTION_ENABLED = "true"$env:ART_MCP_PORT = "8000"$env:ART_MCP_HOST = "0.0.0.0"$env:ART_AUTH_TOKEN = $TOKEN
uvx atomic-red-team-mcpLinux Deployment
# Install uv
curl -LsSf https://astral.sh/uv/install.sh | sh
# Generate secure token
TOKEN=$(openssl rand -hex 32)echo "Linux server token: $TOKEN"
# Configure environment
export ART_MCP_TRANSPORT="streamable-http"export ART_EXECUTION_ENABLED="true"export ART_MCP_PORT="8000"export ART_MCP_HOST="0.0.0.0"export ART_AUTH_TOKEN=$TOKEN
uvx atomic-red-team-mcpmacOS Deployment
# Generate secure token
TOKEN=$(openssl rand -hex 32)echo "macOS server token: $TOKEN"
# Launch server
export ART_MCP_TRANSPORT="streamable-http"export ART_EXECUTION_ENABLED="true"export ART_MCP_PORT="8000"export ART_MCP_HOST="0.0.0.0"export ART_AUTH_TOKEN="$TOKEN"
uvx atomic-red-team-mcpVerify whether the MCP servers are running.
Test each server
curl http://10.2.20.14:8000/health # Windowscurl http://10.2.20.15:8000/health # Linuxcurl http://10.2.20.16:8000/health # macOSNote: These commands are for initial setup and testing. For production use, implement proper service management with systemd, scheduled tasks, or launch daemons.
Step 2: Enable Unified Control
Next, you’ll connect all servers to your AI assistant. Replace the bearer tokens in the configuration below with the tokens you saved from the previous step.
{ "mcpServers": { "atomic-windows": { "command": "npx", "args": [ "-y", "mcp-remote", "http://10.2.20.14:8000/mcp", "--header", "Authorization: Bearer abc......windows", "--allow-http" ] }, "atomic-linux": { "command": "npx", "args": [ "-y", "mcp-remote", "http://10.2.20.15:8000/mcp", "--header", "Authorization: Bearer def......linux", "--allow-http" ] }, "atomic-macos": { "command": "npx", "args": [ "-y", "mcp-remote", "http://10.2.20.16:8000/mcp", "--header", "Authorization: Bearer ghi......macos", "--allow-http" ] } }}Restart your client, and Claude will have direct access to atomic testing capabilities across all three major operating systems.
Multi-Platform Attack Scenarios
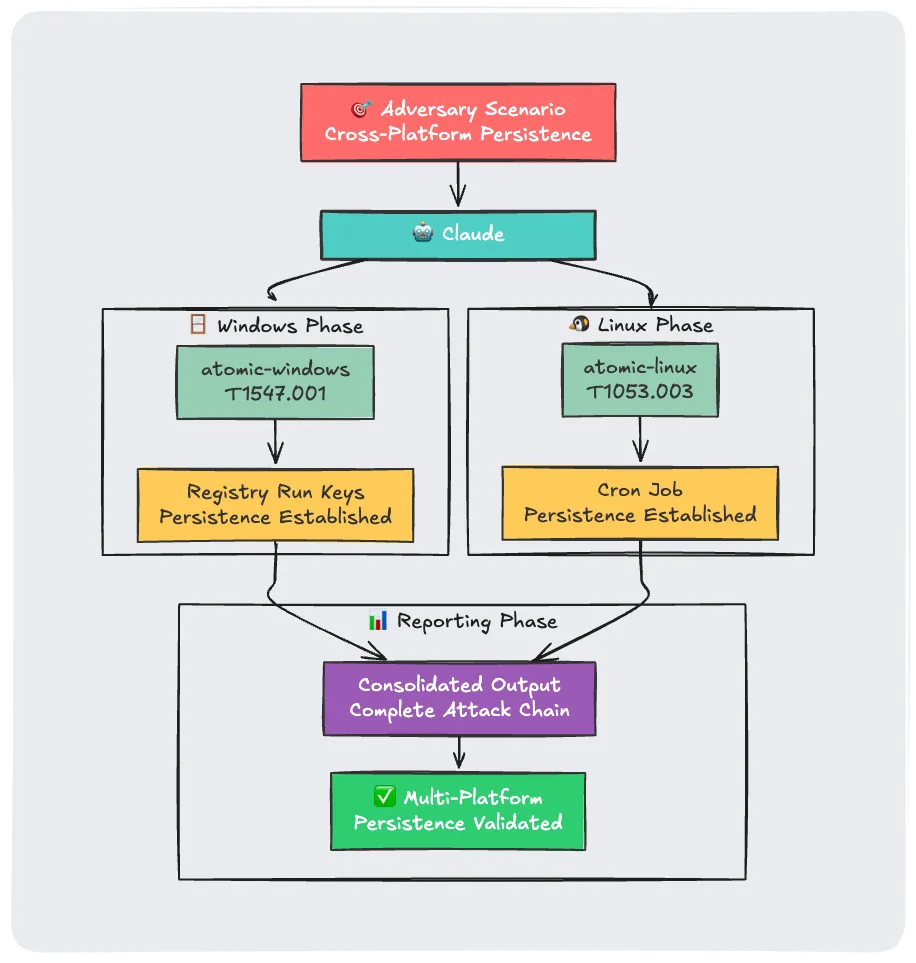
Scenario 1: Run Persistence atomics across all platforms
Imagine simulating an adversary who establishes persistence on Windows through registry manipulation, then moves to a Linux system using cron jobs:
Execute registry persistence atomic test on atomic-windows server, then immediately follow up with a cron persistence test on atomic-linux server
Claude coordinates both attacks:
- Windows Phase: Executes T1547.001 (Registry Run Keys) on the Windows server
- Linux Phase: Executes T1053.003 (Cron) on the Linux server
- Reporting Phase: Provides consolidated output showing the complete attack chain
Here is a sample output on what that would look like.
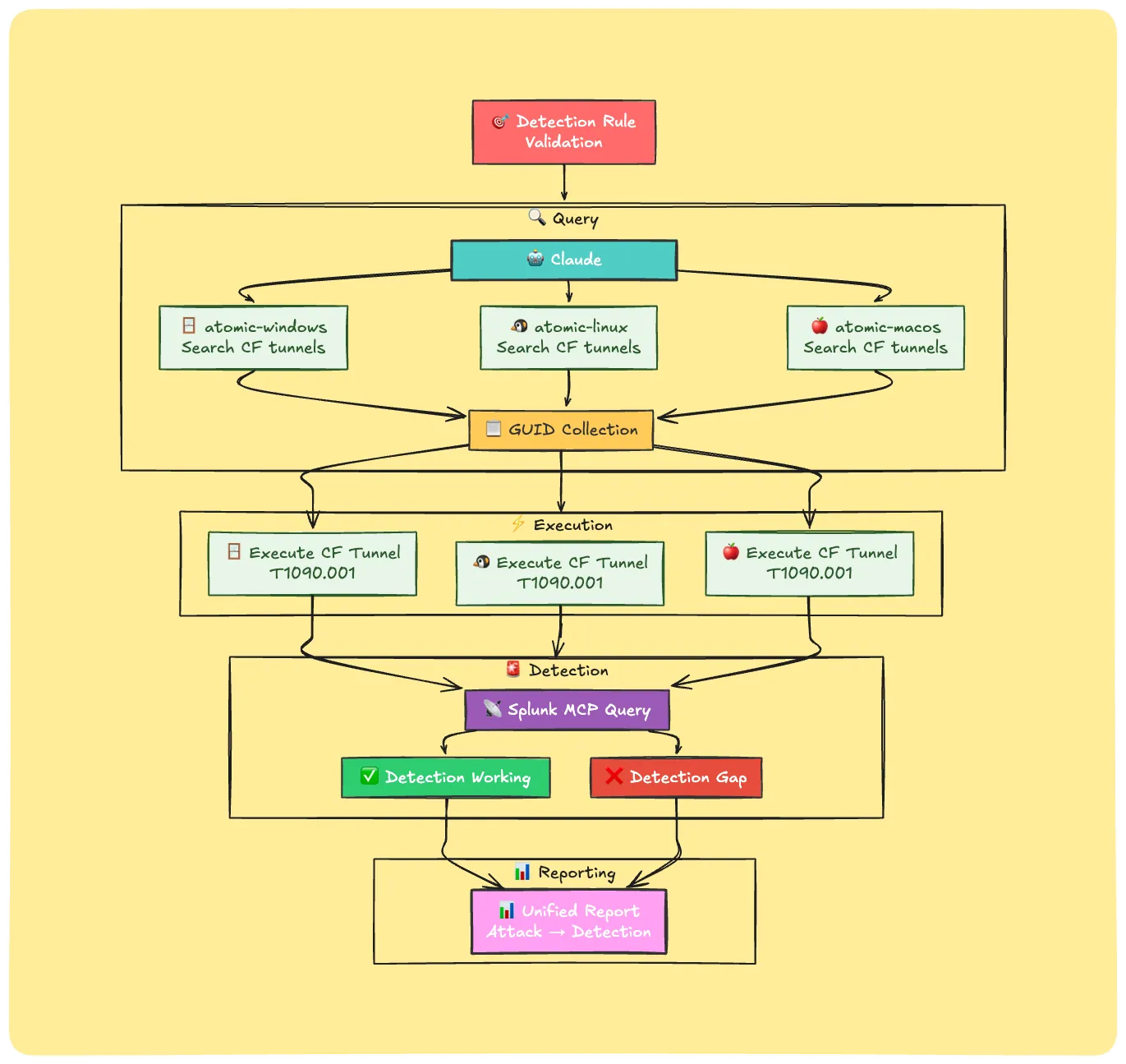
Scenario 2: Detection Rule Validation
Ever wondered how to efficiently execute atomic tests across Windows, Linux, and macOS—and get immediate validation results for your entire detection stack?
For example: Want to assess your detection coverage against “Living off the tunnels” techniques? Run Cloudflare tunnel atomics on every major platform and instantly check whether your rules trigger the right alerts
My detection rule targets Cloudflare tunnels. Find and execute Cloudflare tunnel atomics on atomic-windows, atomic-linux, and atomic-macos to validate detection coverage across platforms.
After execution, query Splunk MCP and see whether there are any alerts for Cloudflare Tunnels.
Claude will
- Query: Queries and retrieves the atomic GUIDs for Cloudflare tunnel across all MCPs.
- Execution: Automatically finds and executes the Cloudflare tunnel atomic across Windows, Linux, and macOS.
- Detection: Checks Splunk MCP for any new Cloudflare alerts triggered by these activities.
- Reporting: Summarizes the entire lifecycle of the attack, from execution all the way to detection outcomes.
Scenario 3: Threat Intelligence to Multi-Platform Playbook
Remember those advanced prompts from Part 1? They become even more powerful with multiple platforms:
Analyze this threat intelligence report and find platform-specific atomic tests. Execute Windows-specific TTPs on atomic-windows, Linux TTPs on atomic-linux, and macOS TTPs on atomic-macos. Provide a unified execution report.
Claude will:
- Parse the threat intel for TTPs
- Map TTPs to platform-specific atomic tests
- Execute tests on appropriate platforms
- Generate a comprehensive multi-platform assessment

What’s Next?
This enables several use cases:
- Automated kill chain execution across multiple platforms
- Purple team exercises with real-time coordination
- Threat hunting validation across heterogeneous networks
Important
With great power comes great responsibility. Use these capabilities in isolated, controlled environments, on systems you own or have explicit permission to test.
This AI-powered orchestration approach opens up many possibilities, and I am curious about your experiences:
- Have you tried orchestrating security testing across multiple operating systems? What worked well, and what didn’t?
- What pain points have you faced with distributed testing or automating your security workflows? Are there specific bottlenecks that AI coordination could solve?
- Are there use cases, specific techniques, or atomic tests you’d like to see AI-powered orchestration handle better? What would make this approach more valuable for your team?
- Submit your toughest orchestration scenario. I’ll respond or feature solutions in future posts.
Additional Resources
- Source code: GitHub
- Bug Reports: Create an issue
- Questions: Find me on Atomic Red Team Slack
- Setup guide: See the installation instructions
- Advanced configuration: Check the complete documentation for production setup (service management, troubleshooting, and SSH tunneling)